The Three A's
This lesson explores the three A's of network security: Authentication, Authorization, and Auditing
We'll cover the following
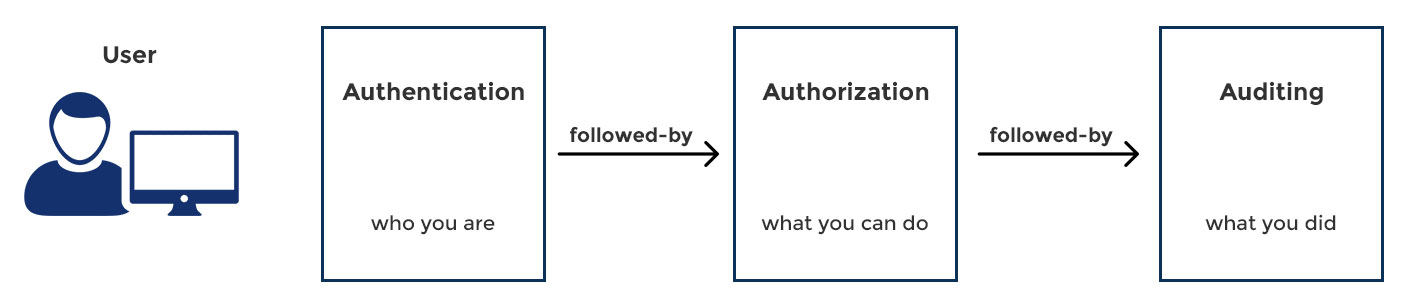
All network security schemes have three core components:
- Authentication
- Authorization
- Auditing
Each of these facets serves a distinct purpose in a network security scheme that we will examine, one by one, below:
Authentication
Authentication is the act of validating that users are who they claim to be; it is the process of verifying the identity of a person or device. Passwords are the most common authentication factor. If a user enters the correct password, the system assumes the identity is valid and grants access to the user. Other authentication mechanisms, such as one-time pins, authentication apps, and even biometrics (retina scan, fingerprints, etc.), can be used to authenticate identity. Many web services allow users to enable * two-factor authentication*, also known as 2FA. In some instances, systems require the successful verification of multiple factors before granting access. Attacks against authentication systems are typically performed in a brute-force manner where an attacker uses a computer program that tries one combination after another until the user’s password is found.
Authorization
Authorization is often confused with authentication, but the two have stark differences. Authorization refers to granting or denying access to specific resources based on the requesting user’s identity. This term is often used interchangeably with access control or client privilege. Some good examples of authorization are giving someone permission to download a particular file on a server or providing individual users with administrative access to an application. In secure environments, authorization always follows authentication. Users first prove that their identities are genuine before an organization’s administrators grant them access to the requested resources.
To clarify the distinction between authentication and authorization, consider a scenario where you board a plane with an economy-class ticket. You prove your identity to the airline agent at the gate using your boarding pass. The gate agent confirms that you are who you claim to be and allows you on the plane. However, you aren’t authorized to sit in the business or first-class compartment since you only hold the privilege to travel in economy class. In other words, you are authenticated to travel but not authorized to travel by first or business-class.
Auditing
Auditing is the act of logging events generated from authentication and authorization. This lof may also include other activities that are considered significant from a security perspective. Auditing, also known as accounting, is the process of keeping track of a user’s activity while accessing the network resources, including the amount of time spent in the network, the services accessed while there, and the amount of data transferred during the session. If proper authentication, authorization, and accounting mechanisms have been established, a person cannot deny their own actions. In security lingo, this is known as nonrepudiation. Examples of nonrepudiation include log-in/log-out, attempting to perform a privileged action, modification of an important financial record, download of sensitive data, amount of data transferred, etc. The audit log records all user actions and can be reviewed by an administrator. Usually, auditing data is used to identify malicious patterns or trends, detect breaches, undertake forensic investigations, etc. In recent times, the case of Anthony Levandowski is an example of someone who was audited and sued by Google for downloading sensitive and secret documents from Google servers and taking them with him to his new job at Uber. Auditing makes the detection of such illegal activities possible. To continue with the airplane analogy, auditing would be akin to the crew observing passengers mid-flight for any unusual or threatening behavior, like an air marshal.
In the next lesson, we’ll look at encryption and message integrity.