What is a phishing attack?
A phishing attack steals personal information or essential credentials by deceiving users to click a malicious link (presented as one from a trusted party).
Phishing is a tool to install ransomware, virus, or spyware in user systems. It can be categorized among the types of social engineering attacks.
Consequences of a phishing attack may include identity theft, unauthorized purchases or leakage of account details to an unknown party for individuals, and loss of confidential data, company policies, and necessary system details for organizations.
How does phishing work?
Following is the procedure that leads to a phishing attack:
- Attackers target a specific individual, group, or organization.
- A malicious link is sent to the targeted audience masked as an authentic link. This link can be sent via text, email, or other communication media.
- Users click on the link redirecting them to a page that requires their credentials or a page that downloads malicious software into their computers.
- This enables the attackers to gain unauthorized access to user data.
Types of phishing attacks
Phishing attacks can be divided into the following two categories:
Email scams
Attackers send the generated email link to thousands of users on the internet via email to gain profits. They go to extreme lengths to mimic an original email from an organization making it seem trustworthy. This puts users into a state of delusion, and they succumb to trusting the link. Even a few users clicking the link will enable the attackers to gain information or make profits.
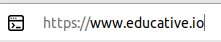
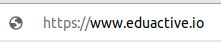
These kinds of emails are usually similar to their original counterparts. The difference can be noted in the URL where misspelled, extra, or fewer domain names may be present. Another characteristic of this type of phishing is that the email sent might require a timely call to action from the users. Thus, persuading users to access that link as soon as possible.
Original link
Similar link but misspelled
Spear phishing
This is a type where specific individuals, groups, or organizations are targeted instead of targeting random users. These individuals or groups may belong to a government institution. Attackers monitor an organization's internal workings, policies, and procedures and create protocols to gain access to sensitive user data.
A situation based on spear phishing might follow these steps:
- The attacker monitors how students communicate with their peers and instructors.
- The attacker sends an email to students, masquerading as an instructor, that follows the same pattern and guidelines used by the other instructors.
- The redirected link may require the students to log in to their accounts.
- The attacker now has access to the students' login credentials.
- This compromises the student accounts and all the other accounts linked to them.
Prevention
Following procedures could be taken to avoid a phishing attack:
- Spreading awareness: Organisations may conduct phishing awareness boot camps and employee training.
- Multi-layered security protocols: Organisations may add several layers to their network structure, making it difficult for attackers to breach the environment.
- Two-factor authorization (2-FA): Individuals may add two-factor authorization to their accounts to strengthen account security.
- Password policies: It is recommended for users to update their passwords frequently and not to use the same password for multiple accounts
Free Resources