What is Node crypto.DiffieHellman(options)?
What is the Diffie-Hellman key exchange?
The Diffie-Hellman key exchange was one of the foremost vital developments in public-key cryptography, and it’s still often enforced during a variety of today’s completely different security protocols. It permits two parties who have not previously met to securely establish a key that can be used to secure their communications. The JavaScript crypto.diffie-Hellman() technique is employed to form a predefined diffie-HellmanGroup key exchange object.
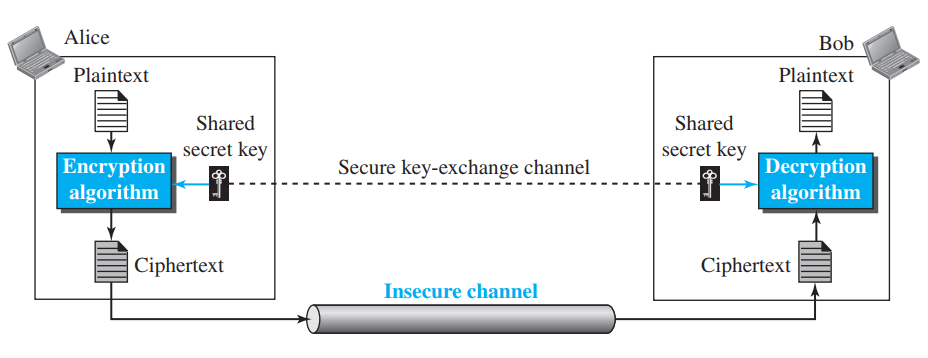
Schema of symmetric cryptography
A Diffie-Hellman algorithm is employed for the aim expressed below. As its name suggests, it’s used for establishing an encryption key.
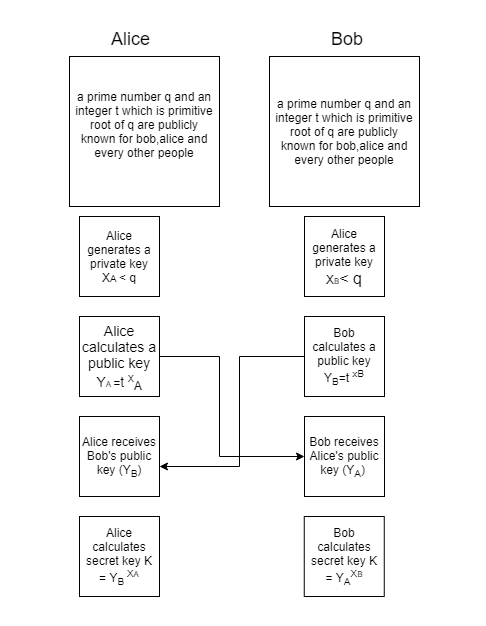
The best way to explain this is using a diagram, which is below:
Calculating Secret And Public Keys
There are a number of things to say regarding the above figure:
- The only factor that every participant ought to hold for themselves is the chosen private keys. Anyone will know all the different parameters.
- The final calculated keys for both participants are the same.
- We can produce very, very large prime numbers, so iterating over all possible candidates for the secret key, called a brute force attack, is computationally impossible.
Implementation with Node.js
In Node.js, the library used for generating the required argument is the built-in crypto library, which provides the programmer with many encryption tools.
const crypto = require('crypto');// Calling two getDiffieHellman method// with its parameter, groupNameconst diffiehellmangrp1 = crypto.getDiffieHellman('modp14');const diffiehellmangrp2 = crypto.getDiffieHellman('modp14');// Generating keysdiffiehellmangrp1.generateKeys();diffiehellmangrp2.generateKeys();// Computing secretconst diffiehellmangrp1sc = diffiehellmangrp1.computeSecret(diffiehellmangrp2.getPublicKey(), null, 'hex');const diffiehellmangrp2sc = diffiehellmangrp2.computeSecret(diffiehellmangrp1.getPublicKey(), null, 'hex');// Checking if both the secrets are same or notconsole.log(diffiehellmangrp1sc === diffiehellmangrp2sc);
In a realistic application, both client and server should implement the procedure above, at the beginning of communication. The server can store the key of cryptography in session, and the client can store it in local storage.
const finalSecret = bob.computeSecret(aliceKey);
Participants use a symmetric algorithm like AES to encrypt the message. To do this, we first install the aes-js library, and then we have the following:
let aesjs = require('aes-js')let fe = aesjs.utils.utf8.toBytes(key_exchang_arguments.y_of_a);let aesCbc = new aesjs.ModeOfOperation.cbc(key, iv);let encryptedBytes = aesCbc.encrypt(textBytes);
Finally, you can send encryptedBytes as a message to your participant.
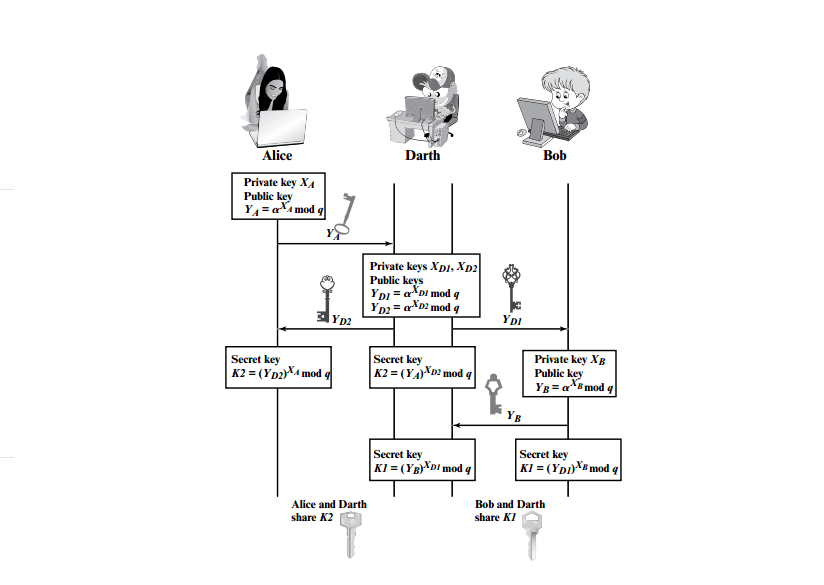
Vulnerabilities
Although diffie-hellman is stable in opposition to passive eavesdropping, we are able to eavesdrop by replacing messages via the usage of man-in-the-middle-assault. We recommend that you observe this in the step by step info of the method in “Cryptography and Network Security: Principles and Practice.” By the way, we present a figure from that source which explains the summary of the attack. You can witness someone else pretending to be the actual participant and beginning to send messages.
Cryptography and Network Security
Authentication and digital signatures are the solution to this vulnerability, so that Bob can ensure that it is Alice who sends him the message.
Conclusion
Cryptography algorithms may be classified into two types: the ones which use the equal key on each side, symmetric, and ones which use distinctive keys on sides.
Uneven cryptography has advantages. For example, it reduces the range of required keys considerably. It is computationally intensive, so the higher technique is to apply uneven cryptography to percentage the important things and steady symmetric encryption. In this article, we went through that.