What is Node crypto.generateKey(type, options, callback)?
What is cryptography in Node.js?
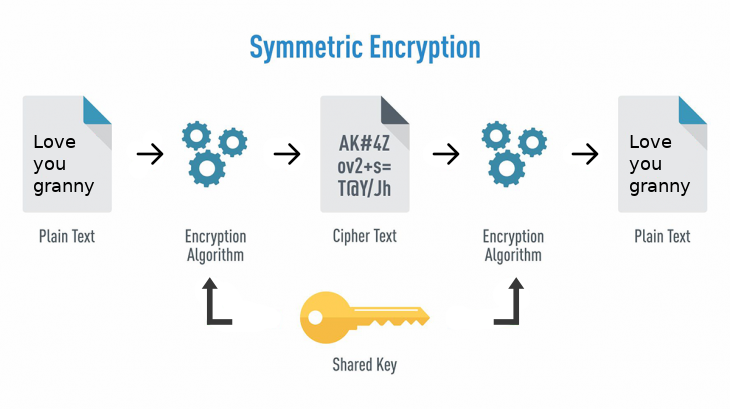
Cryptography is a method of changing plain text into unreadable text and vice-versa. With cryptography, only the sender and receiver of the information can comprehend its content.
With cryptography in Node.js, passwords get hashed and deposited in a database so that data cannot be converted to plain text when it’s hashed, it can only be verified. If malicious actors were to get ahold of your information, they would not be able to decode the encrypted information.
The kind of encryption you make use of in your application depends on your needs. For example, cryptography can be
What is the Node.js crypto module?
The Node.js crypto module makes use of cryptographic functions to assist you in securing your Node.js app. It comprises of a set of wrappers for OpenSSL’s HMAC, hash, decipher, cipher, sign, and verify functions.
‘Crypto’ is incorporated into Node.js so that it doesn’t require a rigorous implementation method or configurations. In contrast to alternative modules, you don’t need to install Crypto before you use it in your Node.js application.
There are several built-in classes in the crypto module. These assist in performing various crypto-related functions, as explained below.
Crypto has the capacity to hash plain text by making use of a hash class that can produce fixed length, deterministic, collision-resistant, and unidirectional hashes. Unlike encrypted data, we cannot decrypt a password with a predetermined key in hashed data. An HMAC class is responsible for a Hash-based Message Authentication Code, which hashes both keys and values to create a single final hash
The Cipher and Decipher are useful in encrypting and decrypting user data for transmission purposes. Data can be encrypted using the Cipher class and decrypted using the Decipher class.
To ensure that encrypted or hashed passwords are valid, you can make use of the verify class. Certificates can also be signed using the sign class.
crypto.generatorKeyPair()
The crypto.generateKeyPair()’ method is a built-in
Syntax
crypto.generateKeyPair(1,2,3)
Parameters: This crypto method accepts three parameters, as seen above in the parenthesis and described below:
1. type parameter: It holds a string and must include one or more of the following algorithms: ‘rsa’, ‘dsa’, ‘ec’, ‘dh’, etc.
RSA: Stands for Rivest, Shamir, and Adleman, the surnames of those who described this algorithm. RSA is an asymmetric cryptography algorithm that uses a public and private key system for secure data transmission.
DSA: A Digital signature algorithm is a federal information processing standard for digital signatures. It involves four processes, of which include Key Generation, Key Distribution, Signing, and Signature Verification.
EC: The Elliptic Curve Cryptography (ECC) is a modern family of public-key cryptosystems based on the algebraic structures of the elliptic curves over finite fields and on the toughness of the Elliptic Curve Discrete Logarithm Problem (ECDLP).
DC: Stands for Diffie–Hellman (DH) Algorithm, a key exchange protocol that lets two parties pass secret information over a public channel without it being transmitted over the Internet. DH enables the use of a public key to encrypt and decrypt conversations between two parties or data using symmetric cryptography.
2. options parameter: Is of type object. It can hold the parameters described below:
modulus length: It holds a number, is the key size in bits, and is applicable for RSA and DSA algorithms only.
public exponent: a number that is the Public exponent of RSA algorithm. Its default value is 0x10001.
divisor length: A number that is the size of q in bits of DSA algorithm.
named curve: A string that is the name of the curve to be used in the EC algorithm.
prime: It holds a buffer and is the prime parameter of DH algorithm.
prime length: A number that is the prime length of the DH algorithm in bits.
generator: A number that is the custom generator of the DH algorithm. Its default value is 2.
groupName: It holds a string. It is the Diffie-Hellman group name of the DH algorithm.
public key encoding: It holds a string.
private key encoding: It holds an Object.
3. callback: A function, with parameters publicKey, privateKey, and err.
err: holds an error.
publicKey: holds a string, buffer, or a ‘KeyObject’.
privateKey: holds a string, buffer, or a ‘KeyObject’.
Return Value: Returns a new asymmetric key pair of the given type.
const { createHmac } = require('crypto');function encrypt(secret){const hash = createHmac('sha256', secret).update('I love cupcakes').digest('hex');return hash}encrypt('abcdefg')// line 9 calls the encrypt function passing into it// the message to be encrypted
Node.js can be built without including support for the crypto module. In such cases, attempting to import from crypto or calling require(‘crypto’) will result in an error being thrown.
When using CommonJS, the error thrown can be caught using try/catch:
let crypto;
try {
crypto = await import('crypto');
} catch (err) {
//this block runs if there
//is an error
console.log('crypto support is disabled!');
}
Conclusion
Cryptography provides security against cyber-criminals.
“An end party that receives encrypted data can decrypt it to plain text for their consumption. Cybercriminals cannot decrypt encrypted data if they do not have the key. This is exactly what the Node.js crypto module does.” - source
Free Resources