What is phishing?
Phishing is the act of using fraudulent emails in an attempt to gain sensitive information about a victim.
A hacker sends an authentic-looking email from a trusted authority, such as a bank, that asks the recipient to download an attachment or click a link. If the victim downloads the attachment, it installs a virus on the victim’s computer (e.g., a keylogger that gains personal data). If the victim clicks on the link, the user is redirected to an authentic-looking website that asks for their credentials. Once the user clicks next, the hacker receives the information and redirects them to the actual webpage.
With the advancements in technology and the introduction of new tools, like phishing kits, these attacks are as widespread today as they were when they first emerged.
Phishing techniques
1. Email phishing scam
An attacker sends out hundreds of authentic-looking emails, as seen in the example below. These emails do not contain any personal information. The hacker believes that a handful of people will fall prey to such techniques and, therefore, their data can be gathered. The hacker spends some time trying to generate an email that mimics the original email as closely as possible. This can trick even the most careful users. The message is usually marked urgent and, therefore, the user will act immediately without confirming that the email is actually from the bank.
2. Spear Phishing
Spear phishing is similar to email phishing in that hackers send an email to the victim. These emails, however, are more targeted and may contain the name and information of that particular user. This builds credibility and, consequently, the user is more likely to fall prey.
3. Whaling
Whaling is similar to an email phishing attack except that it targets high-ranking employees (e.g., CEOs and other high-value targets). These emails claim to require immediate action and are from other corporate or government agencies, which usually ensures that a CEO will click on the attachment and become a victim.
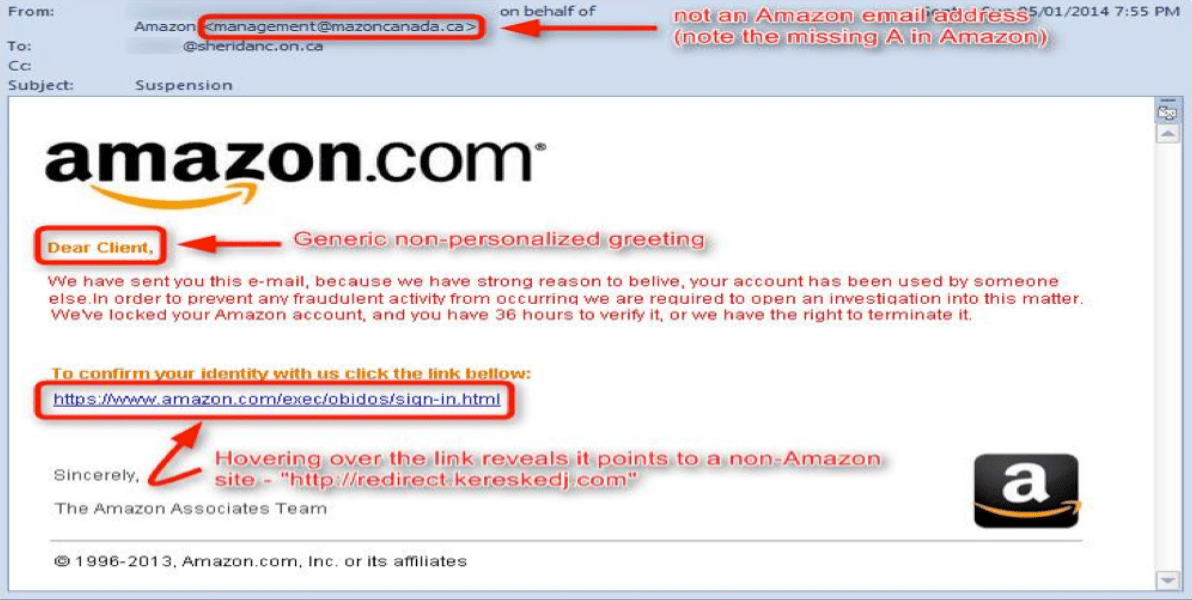
The following image shows an example of a phishing email and the ways to identify its authenticity:
Common features
- Urgent: Phishing emails will usually ask the users to take prompt action as there may be a security risk involved.
- Links: The email may contain links that the user is asked to click to update passwords, login, etc.
- Attachments: The email may contain some attachments that ask to be download.
- Sender: The email will not be sent from an official company, bank, or government email.
- Offers: Offers from supermarkets or online stores that are too good to be true. Free laptops, phones, or huge discounts may be used to lure the victim.
Prevention
- Contact the company personally if verification is required.
- Open the company website by searching the browser rather than clicking the URL.
- Use security software that can detect trojans and viruses.
- Use multi-factor authentication on actual accounts. It is unlikely that the forged website will require multi-factor authentication; therefore, it can be a red flag.
- Check the spellings of the URL that you are re-directed to. Usually, the URL will contain differences such as ‘.org’ where there is usually a ‘.com.’
- Ensure that the connection is https as most companies and banks use an encrypted connection.
RELATED TAGS